
Cybersecurity for Rural Alberta.
Alberta farmers and ranchers are no strangers to the unexpected -- however, computer problems and ransomware shouldn't be as unpredictable as the weather.
Imagine not worrying about ransomware and unreliable computers. ThreeShield also optimizes your systems to minimize the disruptions that come with rural Internet.
That's ThreeShield.
Let's keep the conversation going...
ThreeShield have depth and breadth - have worked with them on network security, data protection, PCI compliance, desktop support and even code reviews. Not sure how they do it, but I highly recommend.
-Christopher (rural meat processing)
Signs you're not backed by IT for Rural Alberta
IT support with limited cybersecurity
The local “IT guy” in town can help set up your wireless and give you basic support, but that's not enough for your operation.
You need reliability. You need to know that the latest ransomware isn't going to affect your feed and water consumption, harvest statistics, calving monitoring, or accounting.
It's time for you to get a hand on keeping your operation, website, and computers running smoothly.
Why doesn't anyone secure farming and ranching tools?
Farmers and ranchers use a wide variety of customized, web-based, and trusted “old” tried-and-true tools. Having ThreeShield on your team means that we hold small-market web-based tools accountable and get them to secure your systems so you get the protection you deserve. We also customize our patch monitoring and update tools to suit your specific needs and make sure you know when you need to update unusual tools -- and, more importantly, when it's okay to to relax and avoid disruption.
Why does my Cyber Insurance cost so much?
Great question. If it does, it might be time to switch IT providers because our foundation is built on auditing and cybersecurity. We make sure you're not just ready for your cyber insurance assessments but that you excel.
At the end of the day, having your business protected by the ThreeShield standards means having us support your team, which actually saves you money.
Check out our Google reviews. Our clients save money on their General Liability, Errors & Omissions, and Cyber Security insurance because our approach makes you look like a lower risk to insurance underwriters.
"Cyber security insurance providers have confirmed they have protected our business well."
- Juliane
Can I take care of this myself?
Rural Alberta was built by hard-working and self-sufficient farmers and ranchers working together to solve the problems in our hash climate. We get it -- and let you cut costs -- by making it easier to take care of tech by yourself when you want, but with the support of experienced cybersecurity experts who take care of the annoying stuff in the background.
If you're looking for customized IT services, your best option is ThreeShield. Call us at 403.538.5053.
You might be wondering...
I live in the middle of nowhere. How can you help me?
We use a few remote support tools to make sure that we can always get to you, even if the roads are blocked. If you need a new computer and we can't get to you in person, we'll get it to you through our network of trucking, bussing, and individual partners to get it to you. We'll walk you through setup and other problems either through remote support in your computer, video calls, or over the phone.I want to accept credit cards; can you help with the compliance that comes with it?
Absolutely. Our experts have been certified as PCI (Payment Card Industry) Internal Security Assessors, PCI Professionals, and stay abreast with the latest PCI requirements. We have set up a straightforward process to get you compliant and maintain your compliance so you don't have to worry about credit card breaches -- or unexpected requests from your bank or insurance company.Do you do third-party assessments?
Yes! While we are experts at providing a full suite of IT security support, the ThreeShield team can provide independent third-party assessments of specialty tools.Our foundation is in auditing for highly regulated industries, governments and Fortune 5 companies. We believe all companies should have access to this calibre of cybersecurity support.
I outsource bookkeeping and other office tasks overseas.
Can you still help me?
ThreeShield has experience working with outsourced providers on every content except Antarctica. If you are using global solutions, your IT support and security need to understand how to balance keeping foreign hackers out while letting in your international team.
We have extensive experience with geographically diverse teams, including overseas bookkeepers, application, and web developers.
Can you secure my WordPress, Financial Tech Tools, Wix, Squarespace, or other website?
Yes, we have a proven process to speed up and secure your site while allowing your web designer to continue working their magic.We'll also secure your Squarespace, Wix, GoDaddy, and other sites; and work with providers like Financial Tech Tools to secure your implementation.
Not ready to switch?
At ThreeShield, we understand switching IT providers is a big deal.
That's why we have a phased on-ramp and work with your existing web designer to improve their services without disrupting your business. In most cases, we can quickly secure your website and email without significant changes and schedule big changes after the tax season wanes.
Staying with standard IT support increases your chances of experiencing a tax time catastrophe. We've taken on disappointed clients from providers who let them down and helped them pick up the pieces after losing data from faulty backups or being breached. It's devastating.
Our proven onboarding process includes reduced rates during a ramp-up phase. We consider any licenses you have already purchased and reduce disruptions during tax season. Our top priority is ensuring your business runs smoothly during your busy season.
This page is about to get technical...
The rest of the page talks about the more technical parts of our services. We usually do these behind the scenes, but most farmers and ranchers are also highly technical and want to know the details, so we're including them.IT Security for a Competitive Edge
ThreeShield’s information security approach makes you your business's hero to enhance your performance, productivity, and reputation, as well as gain trust and loyalty from their customers and stakeholders.
Scalable Information Security
ThreeShield’s cybersecurity solutions are adaptable and scalable to the changing needs and demands of businesses, as well as the evolving threat landscape and regulatory environment from PCI and PII to provincial, Canadian, and global privacy requirements, including GDPR.
From one Microsoft Windows, Mac, or Linux computer to thousands, we grow with you. Our proprietary patching approach will even make sure that your patches don't clog up your network when you grow to have hundreds of laptops, servers, and other network equipment.
Penetration Testing and Vulnerability Assessments
Everything from insurance questionnaires to client and credit card merchant agreements require penetration tests nowadays.
The problem with standard pen tests is that they are often just automated scans or attempts to find the first problem and get in.
Companies that take this approach don't deliver much value. Sadly, when we're hired for follow-up information security audits, we have to look at these scant pen test reports and wonder how other companies can justify calling something an IT vulnerability assessment when they just ran a scan and came up with five IT security recommendations.
ThreeShield takes a comprehensive information security controls approach based on decades of experience auditing everything from Government of Alberta entities and the space shuttle rocket mission control room to fintech startups, accounting firms, primary healthcare networks, military contractors like Sikorsky Helicopters, and ecommerce companies.
Yes, we do run the standard scans, provide Payment Card Industry (PCI) Approved Scanning Vendor (ASV) reports. However, we use that as our starting point -- not the final product. We do a deep dive into potential problems and review all information security controls — within an agreed scope to keep costs down.
This means that we'll often provide over 200 recommendations after another firm — including the Big 4 accounting firms like Deloitte — provided a basic report with 5 or fewer recommendations in their penetration test report.
The best part of our vulnerability assessment process? It involves very little operational disruption.
If you're web-only, it may just involve some short discussions and access to your systems. For large on-premise vulnerability assessments, we'll hook up an assessment device through which we'll run on-site vulnerability and penetration tests.
Since the pandemic and the explosion of hybrid working, many offices are often sparsely populated. This approach avoids disturbing people and avoids having to co-ordinate access.
On-prem Cybersecurity: firewalls, wireless, server, network, and desktop security
When's the last time you updated your switches, routers, and firewalls? Our process includes daily checks to make sure that your systems don't remain vulnerable to newly-discovered problems, patches, and attack approaches.
Many Managed IT Service Providers (MSP) and IT shops often limit information security to Windows patching, backups, and initial configuration of firewalls.
However, maintaining a secure business is a continuous process, which requires continuous firewall configuration updates, wireless monitoring and updates, and changes to computer settings to protect servers, desktops, and laptops from emerging threats.
We also look at your infrastructure design. In some cases, virtualization technologies like Hyper-V and VMware might save you money and increase reliability, for example. In others, moving some infrastructure to the cloud might make your staff more productive and earn more revenue.
Cloud security
We've got you covered to secure your IT cloud. The primary cloud platforms that we support include:
- Amazon Web Services - AWS
- Microsoft Azure
- Microsoft 365 - M365
- Google Cloud Platform - GCP
- Google Workspace
- cPanel
- Cloudflare
- WordPress
- Atlassian - Jira - Bitbucket - Confluence
- GitHub
- QuickBooks
- Xero
- Salesforce
Disaster Recovery, Backups, and Business Continuity
Every time we get called to respond to a new client's ransomware attack, they had already tried to restore their backups.
Nearly every time, the backups were on-premise, on the same computer network as the compromised computers. Both had been ransomwared.
We also find that cloud computing systems are rarely properly secured or backed up. These include email and storage platforms like Microsoft 365 and Google Workspace; virtual private cloud systems like GCP, AWS, Linode, and Azure; development systems like Bitbucket and GitHub; and business systems like Salesforce.
Business Impact Assessment (BIA) and Data Governance
This is why we start our clients on a comprehensive Business Impact Assessment (BIA) exercise to understand what information you have, how long you can live without it, how much data you can afford to lose, and how it has to be secured.
Business Continuity Planning - BCP
Next, we go through your manual processes to understand how your organization could keep working if your primary systems were unavailable. During this process, we also understand the types of sensitive data that you store and transmit through email and other means. This helps to inform your overall data governance and protection approach.
Backups
Like all IT service providers and help desks, we provide backups. However, since we focus on security, we don't just set up something like VEEAM and run away, leaving you to fend for yourself when ransomware or system failures come knocking.
Instead, we first look at how we can optimize your backups.
Can you replicate your Desktop, Documents, and Pictures to Microsoft 365 (M365) or Google Workspace and just back up M365 or Google?
Which users have so much going on that they need to back up their whole workstations?
What servers need to be backed up? Which VMware, Hyper-V, or other hypervisors need to be backed up?
What cloud services like Salesforce, Atlassian, Bitbucket, Jira, Confluence, GitHub, QuickBooks, Dental Practice Management Systems (DPMS), or accounting systems need to be backed up?
What databases, RDS, DynamoDB, or other fragile systems need to be quickly recoverable?
What process do you use for your website backups and updates?
How are your backups isolated from the rest of the environment?
Disaster Recovery Planning
Recovering from a disaster is different than just restoring a backup. It includes DRP testing, notification processes, and correct sequences. We take care of all facets of DRP for you.
Read MoreCode Security - CI/CD - Development Security
Yes, we'll manage your Static Application Security Testing (SAST) and Dynamic Application Security Testing tools.
However, we go a lot farther by manually reviewing your pull requests before you merge them and going over your projects with a fine-toothed comb to find potential vulnerabilities.
Not only will your code become more reliable and secure, but your developers will adopt better practices, become resistant against OWASP Top 10 threats, and meet PCI compliance requirements.
Read More
Incident Response Planning
Plan for the worst; protect with the best.
PCI, privacy regulations, vendor contracts, and insurance forms all require sustainable incident response plans -- in addition to best-in-class security controls.
Why?
Security is an ever-evolving field. Every day, our teams look for the latest new threats. However, it's possible that one day, one will come up before our multiple cybersecurity threat intelligence sources know about them.
If a Zero Day hits, you need to be prepared. Our business continuity planning and disaster recovery planning will play a big piece; however, it's even more important to find a potential breach before it can do enough damage to invoke a BCP or DRP.
This is why we monitor for risky behaviours and activities in everything from Microsoft 365 to AWS. If information is at risk, we'll support you through the incident response plan to make sure that you eliminate or minimize any compliance penalties and reputational damage.
Patching and Security Updates
Of course, you know to apply Windows updates. However, how often do you check:
- Mac OS updates
- Windows optional updates
- Driver and firmware updates
- Non-Microsoft application updates
- Non-Apple application updates
- Linux updates
- WordPress and other web updates
Security Awareness Training and Phishing Simulations
Despite all of our technical protections, the human is still one of our biggest threats.
Staff click phishing emails, get malicious notifications, and introduce viruses to companies more than any other source.
For this reason, we provide comprehensive information security awareness training and phishing simulations to build your staff up and keep your business secure.
Read More
Data Loss Prevention - DLP
Where is your data?
How do your employees protect your data?
Are you meeting privacy and credit card regulations?
If an employee clicks a phishing email, how much client data will be exposed?
These are all questions that your clients and insurance company want to know. It's why we deploy DLP tools as part of our onboarding processes to work with you to develop secure data processing processes.
Security Cameras and Physical Security
We use state-of-the-art network-based camera systems that don't require expensive recording stations and can keep recording during network and power outages.
These smart cameras have AI built in and can interface with your access control and alarm system to monitor for suspicious people verify the identity of employees using access codes or key cards, and even let you look for specific license plates or descriptions of people!
Continuous Monitoring SOC
We continually update our daily, weekly, monthly, and quarterly review processes to reflect new attacks that we discover through threat intelligence and real-time sources.
For example, we include:
- Comprehensive and ongoing vulnerability and information security control assessments to proactively find security and compliance improvement opportunities
- Monitoring for hardware, patch, website, service, backup, cloud (AWS, Azure, Cloudflare Google, Microsoft 365, etc.) security issues
- Daily reviews for server health in addition to real-time alert monitoring
- Proactive responses to login failures
- Reviews for unusual activities in cloud and physical systems
- Proactive firewall monitoring and tweaking
- Upstream provider monitoring for services, such as AWS, Bandwidth, Cloudflare, Google, Microsoft 365, Postmark, Shaw, Bell, Telus, etc.
- Breach detection in addition to best-in-class managed detection and response for viruses, hackers, ransomware, etc.
- Disaster recovery, business continuity, and backup restoration testing
- Custom cloud service monitoring, such as DMS in AWS, VPNs, etc.
- Monitoring for patches that typical MSP tools can't manage, such as unusual Apple software, VMware, Linux, routers, and firewalls
- Deep-dive into security and compliance alerts and reports in Microsoft 365 and Google Workspace.
- Process and system monitoring
- Encryption control and key backup processes to make sure that Windows BitLocker doesn't prevent your staff from working
- Intrusion detection through firewalls, workstation and server tools, and cloud monitoring
- Controls to keep hackers outside of your operating area from getting into your physical and cloud systems
- Layers of security to protect your website administration area from being compromised
What our clients say about ThreeShield

CTO, Tilia Inc. (Financial Technology and Online Payments)
" ThreeShield has employed a dynamic, risk-based approach to information security that is specific to our business needs but also provides comfort to our external stakeholders. I recommend their services. "

VP Operations and Platform Engineering
" Chris [of ThreeShield] possesses the rare skill in security professionals of understanding broader business and technical demands and using that knowledge to develop a balanced approach to security. He skillfully avoids the dogmatic, prescriptive approach to security I've seen all too often and instead builds a security plan that genuinely strengthens the business. "

IT Architect, Financial Technology and Online Retail
" Collaborating with ThreeShield to ensure data security was an exciting and educational experience. As we exploded in growth, it was clear that we needed to rapidly mature on all fronts, and ThreeShield was integral to building our confidence with information, software, and infrastructure security. "

Non-Profit
" Chris at ThreeShield provided really great expertise around our online security needs. His process walked us through a full review in a fun and informative way and then offered practical prioritized recommendations to empower us to boost our productivity and enhance our security without it being too big of a hassle. Chris and his team took us beyond just changing settings. They educated us with valuable tips and tricks that allowed us to evolve and better understand our needs and our audience. The simple changes improved our reliability and reduced risks that were baked into our old process and default web hosting settings. I'd recommend Chris and his team to anyone who knows they need help, or us unsure of what help they need. ThreeShield will take care of you. "

IT Security Director, Linden Lab (Virtual Reality)
" ThreeShield helped us focus our efforts, enhancing our security posture and verifying PCI compliance.
All of this was achieved with minimal disruption to the engineering organization as a whole.
The approach was smart. In a short time, we accomplished what much larger companies still struggle to achieve. "

Senior Director of Systems and Build Engineering
" ThreeShield very much values active and respectful collaboration, and went out of their way to get feedback on policies to make sure proposals balanced business needs while not making employees feel like they were dealing with unreasonable overhead. By doing so ThreeShield really helped change the culture around security mindfulness is positive ways."

Director of Customer Support
" Chris [of ThreeShield] was keen on building partnerships of understanding with key stakeholders, and made the effort to understand the needs of the customer support team in terms of information, and balance those with the regulatory concerns -- both in specific and in general -- over PII, data storage and transmission, etc. It is this proactive approach that ensured that we had an open line of communication with Chris, and made me feel confident that when reaching out to him with a question or concern would net me a direct and actionable response."

Sales Enablement Lead, Precious Metals
" ThreeShield is a really good company to work with. They have a great blend of security and efficiency, making sure that you are 100% secure, but not at the expense of your productivity. 10/10 would use them again. "

IT Analyst, Oil & Gas
" Awesome company, great people to interact with, smart, quick responding, and reasonably priced too. "

Senior Trading Lead, Precious Metals
" Great company to work with! Efficient, secure and always on the ball. Truly a pleasure working alongside Chris & Tyson. Highly recommended. "
Popular Technical Articles

29 January 2024
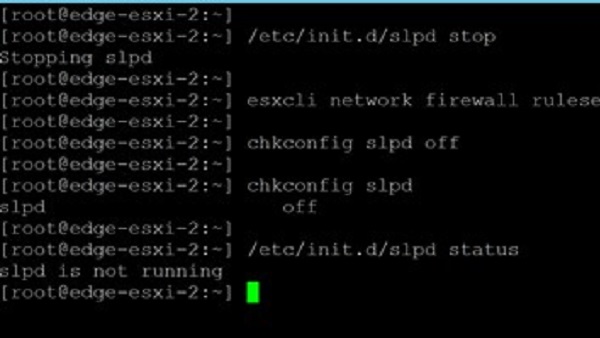
13 February 2023
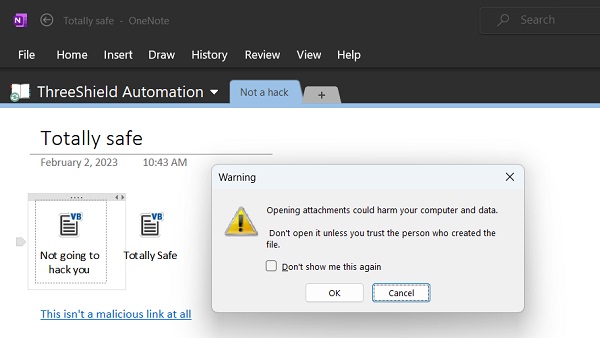
2 February 2023
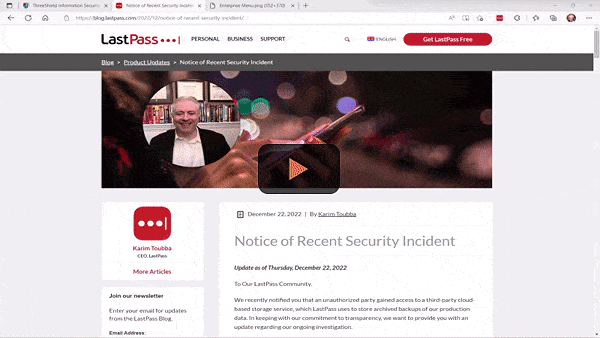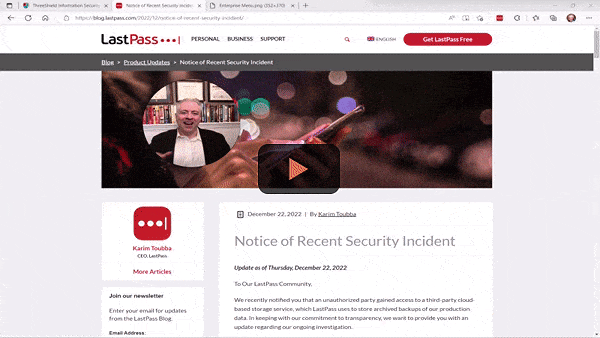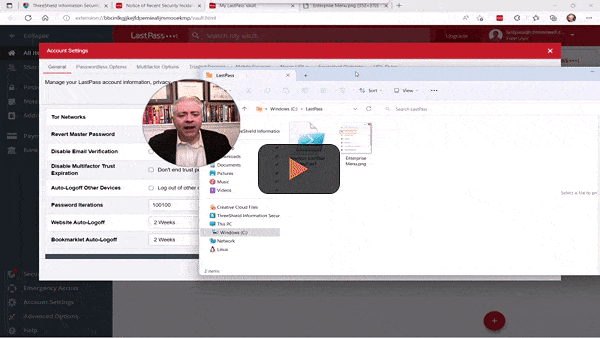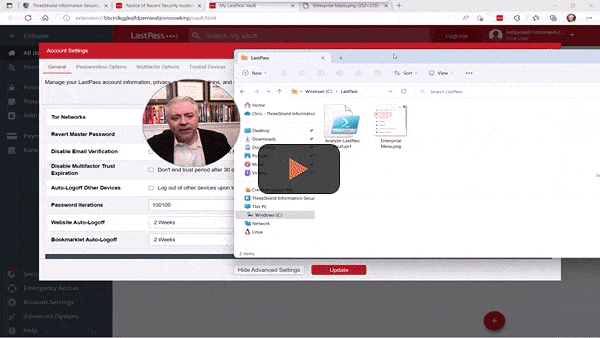
16 January 2023

26 March 2021